When Low Risk Vulnerabilities Attack
When undertaking penetration testing against Internet facing systems, we often see information exposure vulnerabilities. These expose information regarding the systems under test that can, in isolation, be considered low risk as they are not directly exploitable to obtain access to systems or sensitive data.
When triaging these vulnerabilities they should not be overlooked, as the information returned can facilitate other attacks. As an example, in a recent test, an Outlook Web Access server revealed an internal IP address when an HTTP 1.0 request was made to the server, a common vulnerability exposed by OWA servers. Ordinarily this would be flagged and reported to the customer as a low risk concern.
In this instance, however, the systems under test also exposed a web form that provided a SQL connection to an internal server, which allowed a server IP and Microsoft SQL credentials to be submitted:
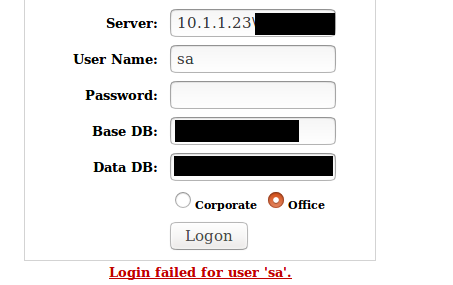
The exposure of the internal IP address via OWA allowed the form to be utilised to attempt connections to each IP address on the extrapolated internal IP address range.
In doing so, we were able to identify three SQL servers on the internal network. On authentication failure to these SQL servers, error messages revealed the internal domain name for the organisation and allowed enumeration of valid usernames via discrepancies in the error messages.
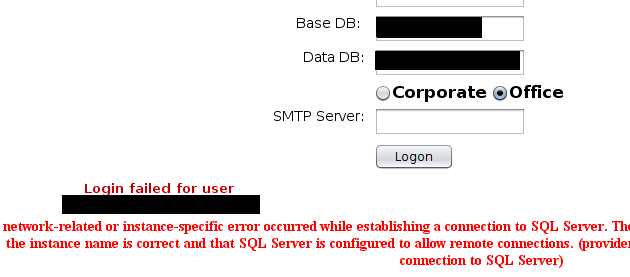
Again, these exposures of domain name and username via error messages would, in isolation, be considered lower risk concerns.
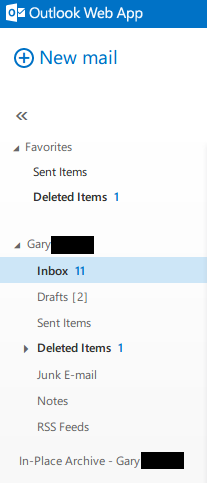
Once the internal domain name and valid usernames were obtained via the SQL login, a common password list was used to identify if any of the users identified used weak passwords. The OWA login page was used to submit the password attempts. A valid credential set was identified, and unauthorised access to emails was obtained.
Our recommendation is to always review all exposures reported via penetration testing, or vulnerability assessments, and understand where combined low risk vulnerabilities can lead to elevated risk. A high-quality penetration test report should provide this level of understanding. It is highly unlikely that a vulnerability scan alone would identify the aggregate risk of low risk vulnerabilities and information exposures.
Improve your security
Our experienced team will identify and address your most critical information security concerns.